Text File Line End DifferencesIndex
Text files contain lines of text delimited by an end-of-line character
(or characters). The line end character in text files is not the same
between Unix/Linux, Windows, and some versions of MacOS.
- A text file written on Unix/Linux contains only a linefeed (
LF)
(sometimes called newline NL) character at the end of each text line.
- A text file written on early MacOS contains only a carriage-return (
CR)
character at the end of each text line.
- A text file written on DOS or Windows contains both a
CR character and a LF character at the end of every line.
Line-end differences may result in “staircasing” text if you send
a Unix/Linux text file to a Windows printer from some programs
(e.g. Notepad). MacOS files may end up over-printed all on one line!
Print a small sample first, and on Windows try using “Write” or “Wordpad”
to read or print a Unix/Linux file instead of “Notepad”.
Some file transfer programs (e.g. WinSCP) will translate line-endings
if they recognize that the file being transferred is a text file
(e.g. because the file name ends in .txt.)
Unix/Linux SCP and SFTP - Secure Copy Program, Secure FTPIndex
For Windows users, scroll down to the Microsoft Windows
Users section.
The SCP and SFTP programs should be used to transfer files between Unix-like
machines when a userid/password is required (e.g. to/from the Course
Linux Server). Both these programs use the underlying SSH (Secure SHell)
protocol that encrypts both your password and the data being transferred.
Avoid the standard FTP program - it sends passwords in clear text
across the Internet. (You are slightly safer using the FTP program
locally here at school, but realize that anyone snooping packets on
your local network will still see your password.)
Unix/Linux: Copy a file from a remote machine to the local machineIndex
Using SCP from a Unix/Linux or Cygwin command line:
$ scp -p userid@remote.host.name:remote_file local_file
The “userid@” part contains your login userid on “remote.host.name”.
You can leave off “userid@” if your remote userid is the same as your
userid on the local machine. You will be prompted to enter your password
for the remote machine. The “remote_file” may be an absolute pathname
(on “remote.host.name”), or it may be a pathname relative to your home
directory on “remote.host.name”. The “-p” option to SCP preserves the
modify time of the transferred file. Examples:
If the remote machine is not behind a firewall and uses a standard SSH port:
$ scp -p abcd0001@acadunix.algonquincollege.com:dodo.txt happy.txt
$ scp -p acadunix.algonquincollege.com:/tmp/foo mydir/bar
If the remote machine is behind a firewall and requires a special port
to be used, the -P option (upper case P) must be used to set the firewall
pass-through port:
$ scp -p -P 2222 abcd0001@example.com:dodo.txt happy.txt
Unix/Linux: Copy a file from the local machine to a remote machineIndex
To copy from local to remote via a Unix/Linux or Cygwin command line,
just reverse the order of the arguments to SCP:
$ scp -p local_file userid@remote.host.name:remote_file
If the remote machine is not behind a firewall and uses a standard SSH port:
$ scp -p happy.txt abcd0001@acadunix.algonquincollege.com:dodo.txt
$ scp -p mydir/foo acadunix.algonquincollege.com:/tmp/bar
If the remote machine is behind a firewall and requires a special port
to be used, the -P option (upper case P) must be used to set the firewall
pass-through port:
$ scp -p -P 2222 happy.txt abcd0001@example.com:dodo.txt
Unix/Linux: Using SFTP (includes Cygwin)Index
The SFTP program is a cover for SSH and SCP that makes things look like
you are using the insecure FTP program; however, the actual connection
and transfer is done using the secure SSH protocol. From a Unix/Linux
(or Cygwin) command line, you can start SFTP like this:
$ sftp abcd0001@acadunix.algonquincollege.com
Connecting to acadunix.algonquincollege.com...
abcd0001@acadunix.algonquincollege.com's password:
sftp> help
[... output similar to using insecure FTP ...]
sftp> quit
If you are familiar with insecure FTP (see below), SFTP will operate
much the same way. As with insecure FTP, you can list the contents of
remote directories and transfer files both ways (using “put” and “get”)
on the same connection.
Some versions of SFTP use -P to set the port number; others have an
awkward way to specify the port number:
$ sftp -oPort=2222 example.com
Connecting to example.com...
idallen@example.com's password:
sftp> help
[... output similar to using insecure FTP ...]
sftp> quit
Unix/Linux Insecure FTP - File Transfer Protocol (do not use)Index
The Course Linux Server does not support insecure FTP, but you can
use SFTP instead with many of the same command meanings.
The old way to move files between machines was the insecure FTP (File
Transfer Protocol) program. FTP is an insecure form of file transfer;
because, any password you type into insecure FTP is visible across the
network. Don’t use insecure FTP for transfer between machines requiring
userids and passwords over an insecure network (e.g. the Internet).
If you log in to the Course Linux Server (using secure SSH), you can then
use the insecure “ftp” or “lftp” commands on the Server to connect out
from the Server to other remote machines (e.g. insecure FTP to your
home computer or to ACADUNIX), if those other machines accept insecure
FTP connections.
If you set up your home computer with an insecure FTP server [be
careful!], you may use the insecure “ftp” command on the Course Linux
Server to connect to your home machine, if your home machine has a public
IP address and isn’t behind a firewall or NAT router. (Use SFTP instead.)
Once you have an insecure FTP connection set up, you can copy files in
either direction using the “put” and “get” commands, as you wish.
Many Internet sites support a form of “anonymous” insecure FTP that lets
you connect to a site without requring a password, using the special
insecure FTP userid “anonymous” or “ftp”. Since it requires no password,
this form of insecure FTP is safe to use over the Internet. It is how
software is often provided for download to Unix/Linux users.
Command-line insecure FTP is a “subsystem” kind of program with its own
set of subcommands. Once inside the insecure FTP program, your prompt
becomes “ftp>”. Inside insecure FTP, the “help” command will list the
possible insecure FTP commands available, and “help commandname” will
give you a bit more help on the given FTP command name.
The Unix manual page for insecure FTP (“man ftp”) explains the individual
insecure FTP subcommands in much better detail.
Do not confuse Unix commands with insecure FTP subcommands. Pay attention
to which program is prompting you for input. To quit FTP, type “quit”.
The command-line insecure FTP program is also available under Windows.
(You may need to install insecure FTP from the Windows CDROM.) The list
of insecure FTP commands is slightly different; but, the basic commands
(ls, cd, get, put) are the same as for Unix. (You can run command-line
insecure FTP from a DOS window or using the “Run” dialog box.) Remember:
FTP is not secure.
Insecure FTP will not transfer entire directories; it may only be used
to transfer files one at a time. (There are ways to get insecure FTP
to fetch multiple files at once; but, the files must all be in the same
directory; you can’t fetch multiple directories. See the help for the
“mget” insecure FTP subcommand.)
Below is an example command-line insecure FTP session to a public
FTP server. This insecure FTP command could be run on a Unix/Linux
machine or under Windows.
$ ftp ftp.gnu.org
Connected to ftp.gnu.org.
220 GNU FTP server ready.
530 Please login with USER and PASS.
Name (ftp.gnu.org:idallen): anonymous # NOTE: special userid used
230 Login successful. # NOTE: no password needed!
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> help
[... many lines of FTP commands show here ...]
ftp> help ls
ls list contents of remote directory
ftp> help get
get receive file
ftp> help cd
cd change remote working directory
ftp> ls
150 Here comes the directory listing.
[... many files show here ...]
ftp> cd gnu
ftp> ls
150 Here comes the directory listing.
[... many files show here ...]
ftp> cd chess
ftp> ls
150 Here comes the directory listing.
[... many files show here ...]
ftp> get README.gnuchess
local: README.gnuchess remote: README.gnuchess
150 Opening BINARY mode data connection for README.gnuchess (89 bytes).
226 File send OK.
89 bytes received in 0.0066 seconds (13 Kbytes/s)
ftp> quit
221 Goodbye.
$ ls -l README.gnuchess
-rw-r--r-- 1 idallen idallen 89 Oct 2 00:49 README.gnuchess
FTP Binary Mode vs. Text Mode file transferIndex
Insecure FTP can transfer files in either “text” or “binary” mode.
Almost always use “binary” mode, which makes an exact copy of the file.
“Text” mode can be used to translate line ends when copying plain
text files between dissimilar systems, e.g. between Unix and Windows,
but the line-end translation will corrupt all other non-text files
(i.e. images sent in text mode will be corrupted).
Insecure FTP vs. the Unix ShellsIndex
The syntax of insecure FTP commands is not the same as the syntax of Unix
commands. This insecure FTP command doesn’t do what you think it does:
ftp> ls -l filename
output to local-file: filename?
If you answer “yes” to this prompt, you will copy the output of “ls
-l” into the file “filename” in your current directory, erasing what
was there before. This is probably not what you want. Don’t do it.
The insecure FTP command names resemble Unix command names; but,
they are not Unix commands. The syntax is different. You are not
typing into a shell, you are typing into the insecure FTP program.
Be careful.
Also, don’t type insecure FTP commands into Unix and expect that they
will work, e.g. the BASH shell doesn’t understand “put filename”.
Microsoft Windows UsersIndex
MS Windows does not ship with any secure file transfer programs such as
SCP or SFTP, even though versions exist that are open source and free
software. You can buy expensive commercial versions of SSH/SCP/SFTP for
Windows from various vendors; or, you can download and install some free
(source code available) programs:
- FileZilla: a multi-platform GUI SFTP, FTP and SCP client.
- WinSCP: a Windows GUI SFTP, FTP and SCP client.
- PuTTY: a program
suite that contains Windows command-line (DOS window) programs that
work like SSH, SCP, and SFTP.
The FileZilla GUI ClientIndex
FileZilla is a free multi-platform
graphical SFTP, FTP, and SCP client. This client is already installed
on the Windows computers in the Algonquin T126 labs.
In the FileZilla Quickconnect bar, enter the Public (or Private)
address sftp://cst8177.idallen.ca in the Host: box and your
Algonquin userid in the Username: box to connect to the Course
Linux Server. Accept the remote SSH host key when prompted to do so.
Upon successful connection, the left side of the window becomes the
Local site: and the right side of the screen becomes the Remote
site:.
Highly recommended for sysadmin: Under the Transfer menu, turn on
“Preserve timestamps of transferred files”.
You can now drag items from Local to Remote or vice-versa. You can
right-click on items for other options.
The WinSCP GUI ClientIndex
WinSCP is a free graphical SCP/SFTP client for
Windows. It has two GUI interface modes: Commander and Explorer.
Use the drag-and-drop Explorer interface if you are not familiar
with the two-pane format of Norton Commander. Use the Commander
interface if you want to move files quickly using drag-and-drop or
mouse-free keyboard shortcuts.
WinSCP lets you edit files locally or remotely directly from the GUI,
but be careful that you don’t make remote edits to files that you later
overwrite with older versions by doing file transfer from your hard drive.
(Remember to fetch the edited remote file after you edit it!)
WinSCP will translate Unix/Linux/Windows Text File Line-End
Differences if the file name is a
recognized text file, e.g. the name ends in .txt.
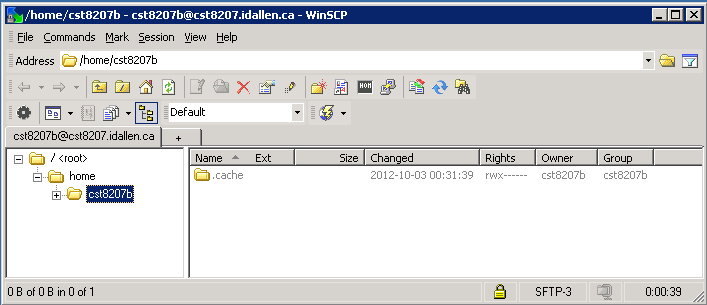
WinSCP is the easiest way to copy files to and from the Course Linux
Server, but it cannot be automated or scripted. For use in scripts,
see the PuTTY suite of programs.
WinSCP Error due to: too large SFTP packet
If you get a WinSCP Error similar to this “Received too large SFTP packet”:
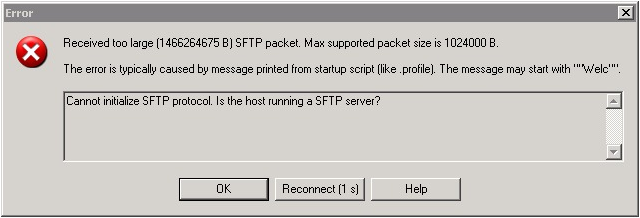
go to your .bashrc file and insert this line at the beginning:
[ -z "${PS1-}" ] && return
Your .bashrc and .bash_profile files must not produce any output
when called in non-interactive mode, otherwise the output confuses the
SFTP protocol.
The PuTTY suite of programs (PSCP, PSFTP)Index
PuTTY is a
graphical telnet/SSH client and a suite of command-line (DOS window)
file transfer clients.
If you download and install the full PuTTY program suite under
Windows (PuTTY comes with an executable auto-installer that will
do this for you), you will find the programs PSCP and PSFTP under
the installation directory (usually under C:\Program Files\PuTTY).
Start up a DOS command prompt, change to this directory, and run
the secure commands you need to copy files to/from other systems.
See below for examples of how to do this.
Unless you change your DOS search PATH, you will only be able to execute
the PSCP and PSFTP commands from the directory into which you downloaded
them.
When transferring files between Windows and Unix/Linux machines,
remember that pathnames on the Windows machines contain backward
slashes while pathnames on Unix/Linux machines contain forward slashes.
For example, you might find yourself typing something like this:
psftp> put "d:\folder\myfile.txt" "public_html/dir/page.txt"
local:d:\dir\myfile.txt => remote:/home/abcd0001/public_html/page.txt
Windows pathnames contain backslashes and the Unix/Linux pathnames contain
forward slashes. Some versions of PSFTP also accept forward slashes for
Windows pathnames. You must surround the pathnames with double quotes
if the pathnames contain blanks.
###PSCP###
PSCP is a command-line copy program, similar to the Unix/Linux SCP program.
If the remote machine is behind a firewall and requires a gateway and
special port to be used, the -P option (upper case P) must be used to
set the firewall pass-through port. Leave it out otherwise.
The backslash at the end of a line below indicates that the line
continues. Type what is written all on one line without the backslash.
C:\> cd "C:\Program Files\PuTTY"
C:\Program Files\PuTTY> pscp -h
...the -h displays a short help listing here...
C:\Program Files\PuTTY> \
pscp -P 2222 "abcd0001@example.com:dir/foo.txt" "folder\bar.txt"
abcd0001@example.com's password:
...only use the -P option if you need the special port number...
...you may be asked to accept the host key here (say yes)...
...file transfers remote "dir/foo.txt" to local "folder\bar.txt"...
You must use your own userid on the remote machine. You must replace
“example.com” with the machine name or IP address to which you wish to
connect. The -P option sets a non-standard port number, if you need it.
Windows pathnames should contain backslashes and the Unix/Linux
pathnames contain forward slashes. Some versions of PSCP accept
forward slashes for Windows pathnames. You must surround the
pathnames with double quotes if the pathnames contain blanks.
###PSFTP###
PSFTP is a secure command-line FTP-like program, similar to standard FTP.
If the remote machine is behind a firewall and requires a special
port to be used, the -P option (upper case P) must be used to set
the firewall pass-through port. Leave it out otherwise.
C:\> cd "C:\Program Files\PuTTY"
C:\Program Files\PuTTY> psftp -h
...the -h displays a short help listing here...
C:\Program Files\PuTTY> psftp -P 2222 abcd0001@example.com
...only use the -P option if you need the special port number...
...you may be asked to accept the host key here (say yes)...
abcd0001@example.com's password:
Remote working directory is /home/abcd0001
psftp> help
...short help listing displays here...
psftp> ls
...listing of directory displays here...
psftp> get ".bashrc" "foo.txt"
remote:/home/abcd0001/.bashrc => local:foo.txt
psftp> put "d:\dir\myfile.txt" "public_html/page.txt"
local:d:\dir\myfile.txt => remote:/home/abcd0001/public_html/page.txt psftp> quit
...file "foo.txt" is now in the current directory...
You must use your own userid on the remote machine. You must replace
“example.com” with the machine name or IP address to which you wish to
connect. The -P option sets a non-standard port number, if you need it.
Windows pathnames should contain backslashes and the Unix/Linux
pathnames contain forward slashes. Some versions of PSFTP accept
forward slashes for Windows pathnames. You must surround the
pathnames with double quotes if the pathnames contain blanks.
The options to the PuTTY Windows version of SFTP (named PSFTP) are
not the same as the options to the Unix/Linux version of SFTP.
In particular, the option “-P” has different meanings!
###Example SCP and SFTP Windows Command Lines###
First, here are some typical PSCP command lines for file transfer from a
local (Windows) computer to the public_html directory of the abcd0001
account on the Course Linux Server. The first line uses the Public
gateway and special port 2222; the second uses the Private IP address
(via the VPN or On-Campus):
pscp -P 2222 d:\dir\image.jpg abcd0001@cst8281.idallen.ca:public_html/a10/image.jpg
pscp d:\dir\image.jpg abcd0001@10.50.254.148:public_html/a10/image.jpg
Second, here is the same transfer using the PSFTP command instead of PSCP:
psftp -P 2222 abcd0001@cst8281.idallen.ca
password:
psftp> put d:\dir\image.jpg public_html/a10/image.jpg
psftp> help
psftp abcd0001@10.50.254.148
password:
psftp> put d:\dir\image.jpg public_html/a10/image.jpg
psftp> help
You must replace abcd0001 with your own userid.
You will be asked for your password on the Course Linux Server.
If you are asked to accept the server encryption key, say “yes”.
You must remember to insert the web directory name “public_html” into
all your file names for the Course Linux Server, since that is
where the web server looks in your account. Files put into your
home directory will not be visible on the Web.
Slashes go backwards for Windows pathnames and forwards for
Unix pathnames.
The psftp and pscp commands may not be in your Windows DOS
search PATH. You can add the directory containing these commands to
your DOS search PATH, or you can change to the directory containing
these commands when you want to run them, or you can type the absolute
path of the command names if you aren’t in the right directory.
Windows Insecure FTP (do not use)Index
The Course Linux Server does not support insecure FTP.
MS Windows has a command-line version of insecure FTP available from a
DOS prompt or in a DOS window. You can also download various graphical
insecure FTP clients. Many recommend the insecure programs “FileZilla”
or “WS_FTP”.
###Using Windows GUI via Windows Explorer###
Some versions of Windows also let you use an insecure FTP URI to
connect to an insecure FTP server and log in and transfer files,
e.g. using this form of URI:
ftp://ftp.algonquincollege.com/
The Windows Explorer (not Internet Explorer!) will let you open an
insecure FTP URI such as the one above and drag-and-drop files between
your machine and a remote machine graphically. Underneath, Windows is
using the insecure FTP protocol and your data and passwords are visible
to anyone who can snoop your network connection. Don’t use this.
You must log in with your own Linux userid.
You will be asked for your FTP password.
Your password and data are not encrypted when you use insecure FTP.
Do not use this method on an untrusted network (i.e. Internet).
You may be able to access a file via FTP that cannot be
displayed in a web browser, since the FTP program is logged in as
your account name and the web browser accesses your files as “other”.
You must ensure that your files have read permissions for “other”
after you transfer them to the Course Linux Server.
Windows Explorer, using insecure FTP, may create directories
and files with the wrong Linux permissions. Directories under
your public_html directory must be readable and searchable (not
writable!) by “other”. Files under your public_html directory
must also be readable (not writable or executable!) by others.
Inaccessible files and directories will generate “Permission Denied”
errors in your web browser. Files and directories with unwanted
“write” permissions will allow other users to delete or erase your
web pages.